I’m Such a Geek
But I enjoy being a geek. This week I’ve been in a VMware training class – Deploy, Secure and Analyze. It’s been a good class. For a lot of it, I already knew the concepts about how things worked, but the class went into a lot of detail of exactly how things worked, and why they work the way they do.
One thing I learned a lot about was the networking portion of it. One of the instructors showed the class a live VMware implementation (It may have been one that he has at home) and gave me an idea. He had his ‘production’ network, his ‘internet’, or public, network, and a ‘DMZ’ network. All of these were attached to physical NICs on his ESX host, but during the lecture we were told that a physical connection isn’t necessarily required. So that gave me an idea.
I have a web server, database server, and file server. My web server, of course, serves web sites and other miscellaneous web stuff. For my more robust websites, it connects to my database server for data storage. My file server is where I keep all my photos and application install files and things. I’ve always known that any public-facing server (i.e., my web server which is accessible from the Internet) should be in a DMZ with its access to other parts of the network restricted. It’s just simple security practice. But I didn’t have a way to do it on my ESXi host. Or so I thought.
I configured my virtual networking so that I had an Internet connection on one virtual switch (we’ll call them vSwitches) attached to my first NIC, my internal servers on another vSwitch using the other NIC (I only have the two NICs), and another vSwitch that is completely internal to the ESXi host. It isn’t attached to any NIC or external switch or anything. My Internet vSwitch is connected to my DSL router. That’s the only thing on that vSwitch. My internal vSwitch has all my servers on it. Except for one. My web server is on my DMZ vSwitch.
I’ve always liked the SmoothWall product (the free one – I don’t like paying for things I don’t have to). Now I like it even more, because it does exactly what I want it to in this setup. For my new firewall, I connected 3 virtual NICs to it, and put one NIC on each vSwitch. I have a GREEN interface (my internal network), an ORANGE interface (My DMZ) and a RED interface (attached to the Internet). Because the firewall is a virtual machine, that is all I need to be able to access my totally virtualized DMZ network. Pretty clever.
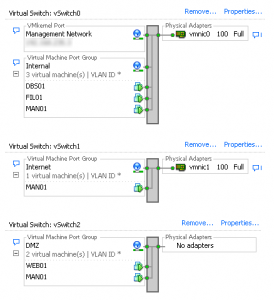 To the left is a diagram of what my virtual network looks like. (Click it to see the full size screenshot) For any of you that have had the pleasure of configuring or managing a virtual network, it should make total sense to you. To anyone that is curious, drop me a line and I’ll explain in more detail if I can.
To the left is a diagram of what my virtual network looks like. (Click it to see the full size screenshot) For any of you that have had the pleasure of configuring or managing a virtual network, it should make total sense to you. To anyone that is curious, drop me a line and I’ll explain in more detail if I can.
So Jacobs paid upwards of $3,000 for me to take this class so I could learn this simple (but clever) network strategy.
Yep, I’m a geek. I’m fine with it though – I don’t have to ask for help with electronic stuff. 🙂

Yeah, I totally get it!
NOT
Huh? We’re glad you’re who you are ’cause we DO need help with electronic stuff. 🙂 Loveya